How to Fix PHP Vulnerabilities: A Step-by-Step Guide for Beginners
Addressing PHP vulnerabilities is crucial for maintaining the security and integrity of websites, as these vulnerabilities can expose your website to various cyber threats, including SQL injections (SQLi). This article equips you with the knowledge and tools to tackle these challenges on PHP remediation, introducing 8iSoft YODA as your comprehensive vulnerability management ally. YODA empowers you, regardless of your cybersecurity expertise, to effectively identify and neutralize PHP vulnerabilities, safeguarding your website’s integrity.
I. Identifying PHP Vulnerabilities with YODA
Imagine a powerful security scanner at your fingertips. That’s YODA! We’ll guide you through scanning a demo site, showcasing YODA’s pinpoint accuracy in detecting critical PHP vulnerabilities.
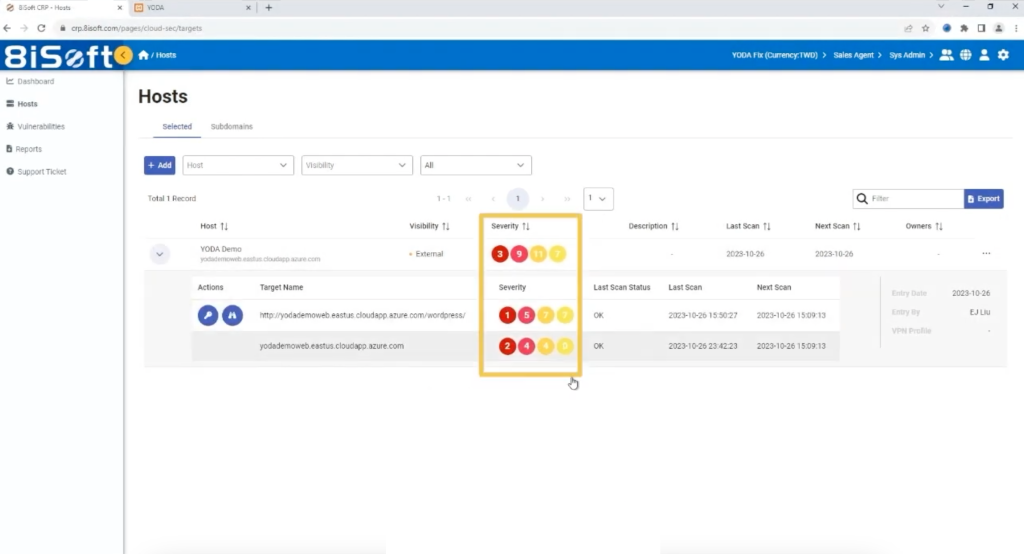

One notable feature of YODA is its risk prioritization mechanism, allowing users to identify and address the most critical vulnerabilities with higher severity levels first. With YODA, you gain a clear picture of the threats lurking within your website, paving the path for effective remediation.
II. Researching Remediation Methods
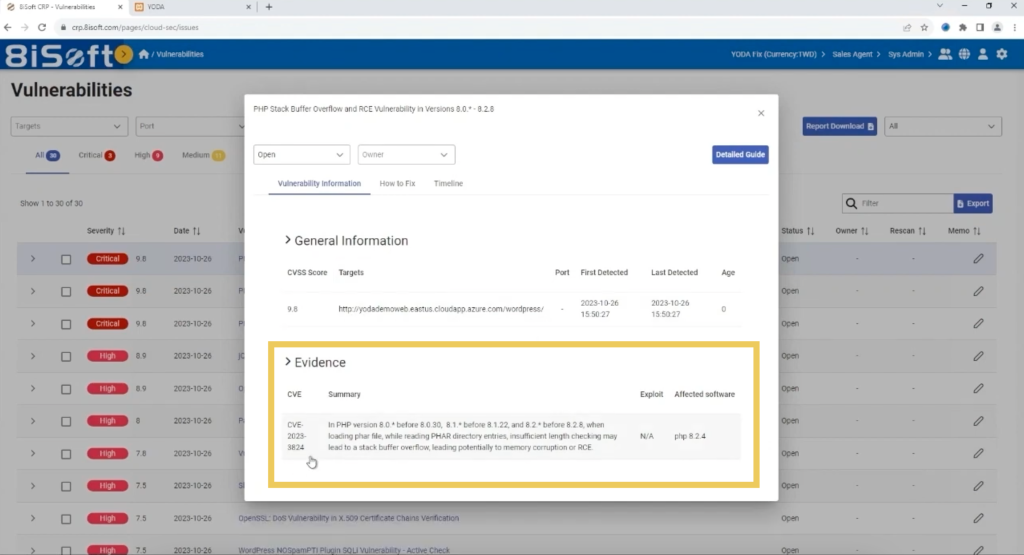
No need to navigate a labyrinth of technical jargon. YODA provides comprehensive evidence sections for each vulnerability, complete with unique CVE numbers. CVE numbers are identifiers for common vulnerabilities and exposures. These numbers act as your passport to a world of online resources, offering precise remediation directions tailored to your specific situation.

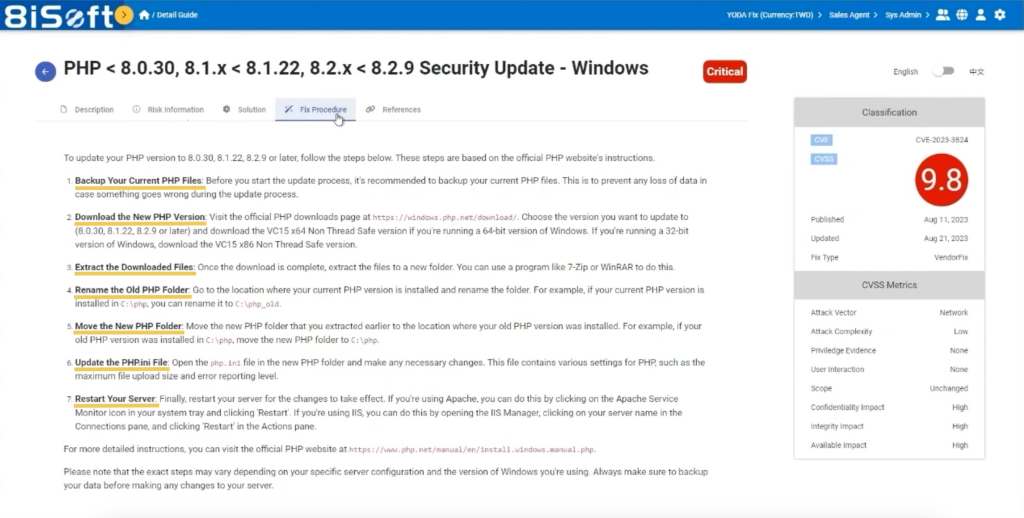
The YODA platform also provides step-by-step remediation plans with their built-in “Detailed Guide” feature. In the Detailed Guide, you will find solution steps on how to fix your vulnerabilities. YODA acts as your personal remediation guide, showing you every single step.

To search for more remediation methods outside of YODA, simply search the unique CVE number in your search engine to find information about these vulnerabilities.
III. YODA’s Remediation Advice
Using a generic PHP remediation advice, “upgrade your PHP version”, as an example. Other vulnerability management vendors would perceive this as a sufficient solution, YODA provides the following simplified yet detailed steps for you to follow through.
Before you start the update process, it’s crucial to back up your current files. This is to ensure that you can still restore your data in case something goes wrong during the upgrade process. YODA walks you through crucial pre-upgrade actions like data backup, ensuring a seamless transition. Downloading and configuring the new PHP version becomes a breeze with YODA’s intuitive interface.
IV. Executing Remediation Steps
Now let us delve into the remediation process in this real-time walkthrough, demonstrating how YODA empowers you to:
- Select the Optimal PHP Version. Visit the official PHP download page at https://www.php.net/downloads.php and download the optimal PHP version for your computer, as recommended by YODA.
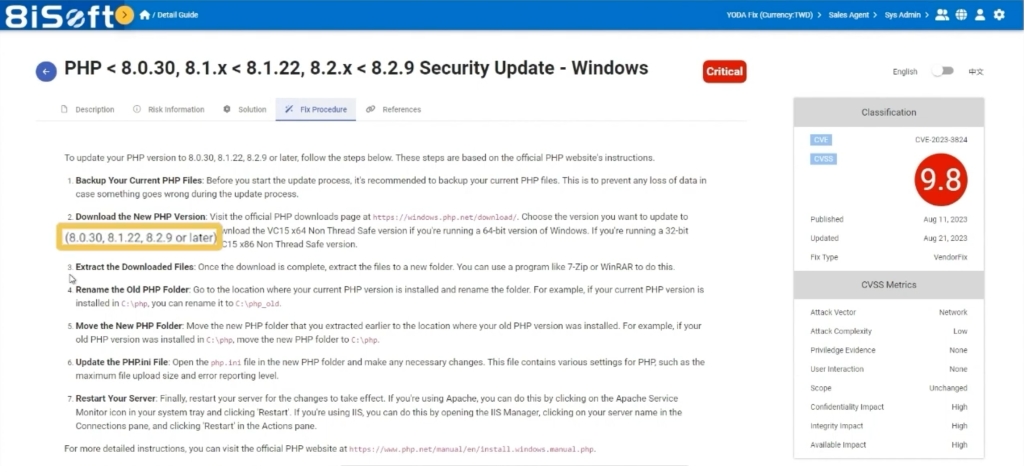

- Download and Extract Necessary files with ease.
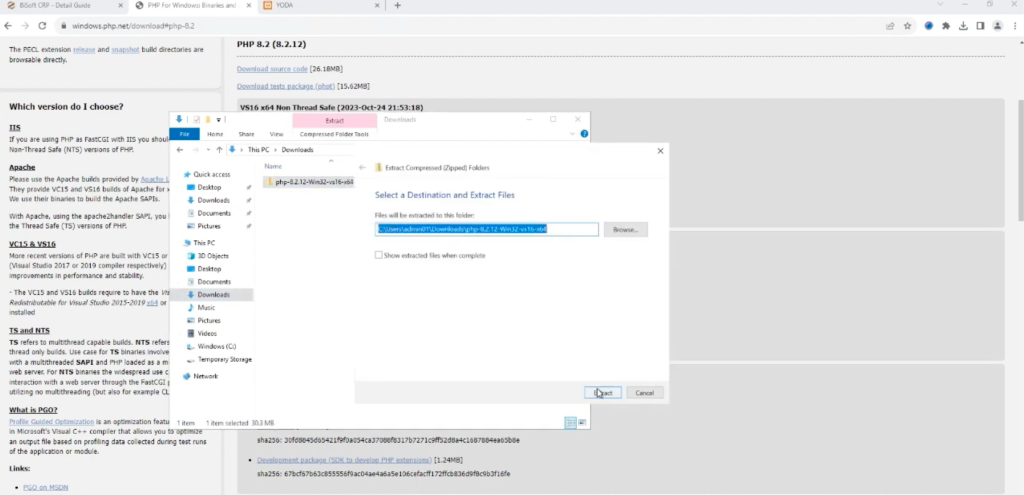

- Rename and Move folders, guided by YODA’s clear instructions.
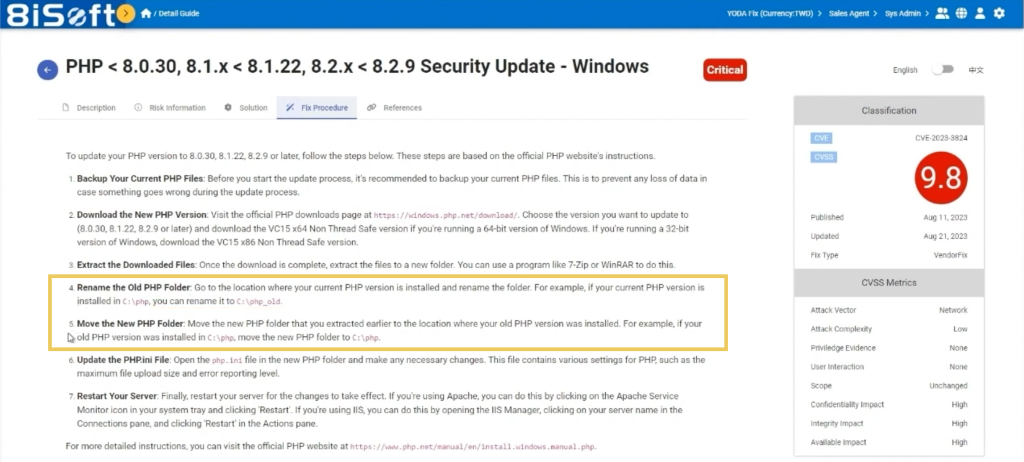

- Update PHP.ini Configuration File accurately.
- Restart your Server for the changes to take effect.
YODA’s intuitive interface ensures you execute each step flawlessly.
V. Verification and Confirmation
To verify that the upgrade was successful, check whether your PHP version has been updated. To check the version you’re currently using, create a new PHP file in your web server directory with the following code:
<?php
phpinfo();
?>
The PHP version should now be the latest version you installed.
VI. YODA’s Post-Remediation Features
After successfully implementing PHP vulnerability remediation measures, it is crucial to ensure that your web applications remain secure through continuous monitoring. YODA allows users to seamlessly return to the platform and check the current vulnerability status of their PHP applications. Users can also initiate comprehensive rescans and review results to confirm that the identified vulnerabilities have been successfully mitigated.
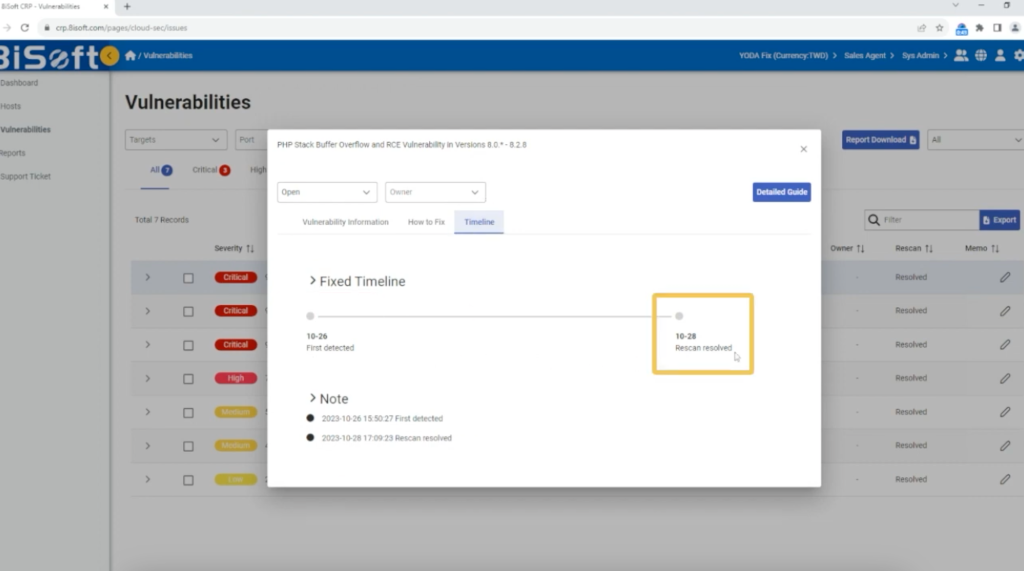
Understanding the chronology of vulnerability detection and remediation is critical for maintaining a proactive security stance. YODA’s “Timeline” feature serves as a valuable resource for tracking the entire lifecycle of vulnerabilities as it documents when a vulnerability was initially detected, as well as the date of successful mitigation. This feature aids in maintaining an organized and well-documented history of security events, which is invaluable for compliance reporting and audit purposes.

VII. Creating Fix Analysis Reports
To further enhance your vulnerability management strategy, YODA also generates detailed website vulnerability fix analysis reports, incorporating valuable insights like WordPress logs.
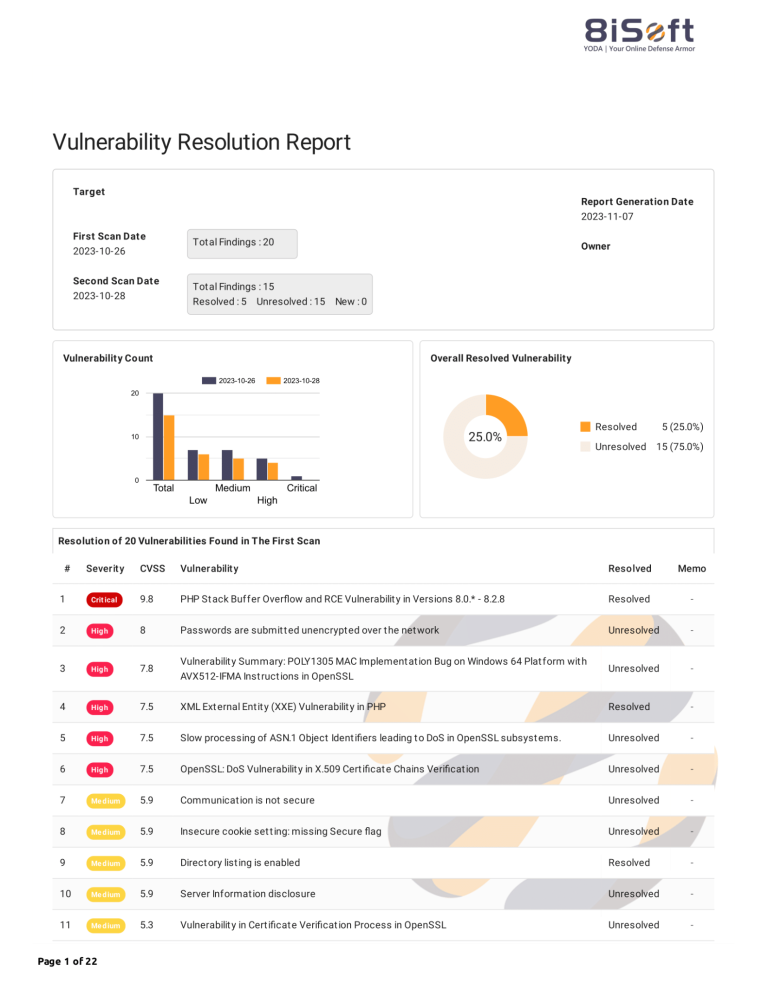

These reports serve as a testament to your proactive security efforts and provide valuable data for future vulnerability management endeavors. It ensures that organizations stay ahead of emerging threats, continuously improve their security posture, and demonstrate compliance with industry standards and regulations.
This guideline has demonstrated YODA’s remarkable capabilities in safeguarding your website from PHP vulnerabilities. Its user-friendly interface, powerful scanning engine, and detailed remediation guidance empower you to take control of your website’s security, regardless of your technical expertise. Remember, vulnerability management is an ongoing process. Embrace YODA as your trusted partner, and navigate the ever-changing landscape of website security with confidence.
🎥 Watch the Tutorial: PHP Remediation with 8iSoft YODA
For a step-by-step guide on PHP remediation using 8iSoft YODA, don’t miss our exclusive tutorial. Click here to watch the video and enhance your understanding of effective vulnerability management.
Stay tuned for the next installment in our vulnerability remediation series. We’ll delve into additional strategies, tools, and best practices to empower you in the ongoing effort to secure your digital assets.
