What are Hackers? Hackers Types: A Comprehensive Guide
The world of hackers is vast and ever-changing, with their categorization depending on evolving communities and terminologies. Delve into the intricacies of hacker types, exploring their motives, and gain insights into safeguarding digital assets. Here’s a closer look at the different types of hackers:
What are hackers?
Hackers, possessing advanced knowledge in computer systems, exploit vulnerabilities for various purposes. This article explores the ethical and malicious applications of their skills.
Why should we be wary of them?
Understanding hackers is crucial as malicious activities can lead to significant personal, business, and governmental damage. This includes identity theft, financial loss, reputational damage, and disruptions to critical services.
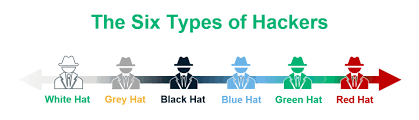

The Eight Different Types of Hackers:
- Black Hat Hackers: Engage in illegal activities for personal gain, causing harm or breaking the law.
- White Hat Hackers (Ethical Hackers): Use skills for authorized security testing, aiding organizations in strengthening defenses.
- Grey Hat Hackers: While not necessarily malicious, they perform unauthorized activities to identify vulnerabilities.
- Script Kiddies: Inexperienced hackers using pre-existing tools without fully understanding them.
- Hacktivists: Use hacking for social or political causes, launching cyberattacks against specific targets.
- State-Sponsored Hackers: Employed or supported by governments for cyber espionage or warfare.
- Insider Threats: Individuals within organizations misusing access for personal gain or malicious purposes.
- Cyber Terrorists: Motivated by beliefs to create fear through large-scale network disruption.
Understanding these types and motivations enhances vigilance in safeguarding digital assets. The complex world of hacking doesn’t always neatly fit into specific categories, and terminology evolves over time.
As the cybersecurity landscape changes, staying updated is crucial. Organizations can implement vulnerability management software as a defense against cyber threats. 8iSoft Yoda, a Risk Mitigation Master Platform, offers a comprehensive framework of Discover, Remediate, and Improvement. This proactive approach significantly reduces the window of opportunity for hackers by facilitating timely patches, updates, and remediation efforts. Stay ahead in the cybersecurity game to protect your digital realm effectively.
