ISO 27001 stands as the global standard for Information Security Management Systems (ISMS), providing a systematic approach to managing sensitive company information. This ensures confidentiality, integrity, and availability. Beyond digital data, ISMS covers physical and human-related aspects of security.
The Guidelines of ISO 27001
The guidelines of ISO 27001 outline requirements and best practices for establishing, implementing, maintaining, and improving an effective ISMS. It employs a risk-based approach, identifying and mitigating potential security risks across a range of controls such as data protection, access controls, incident management, and more.
Quick and Easy ISO 27001 Vulnerability Compliance
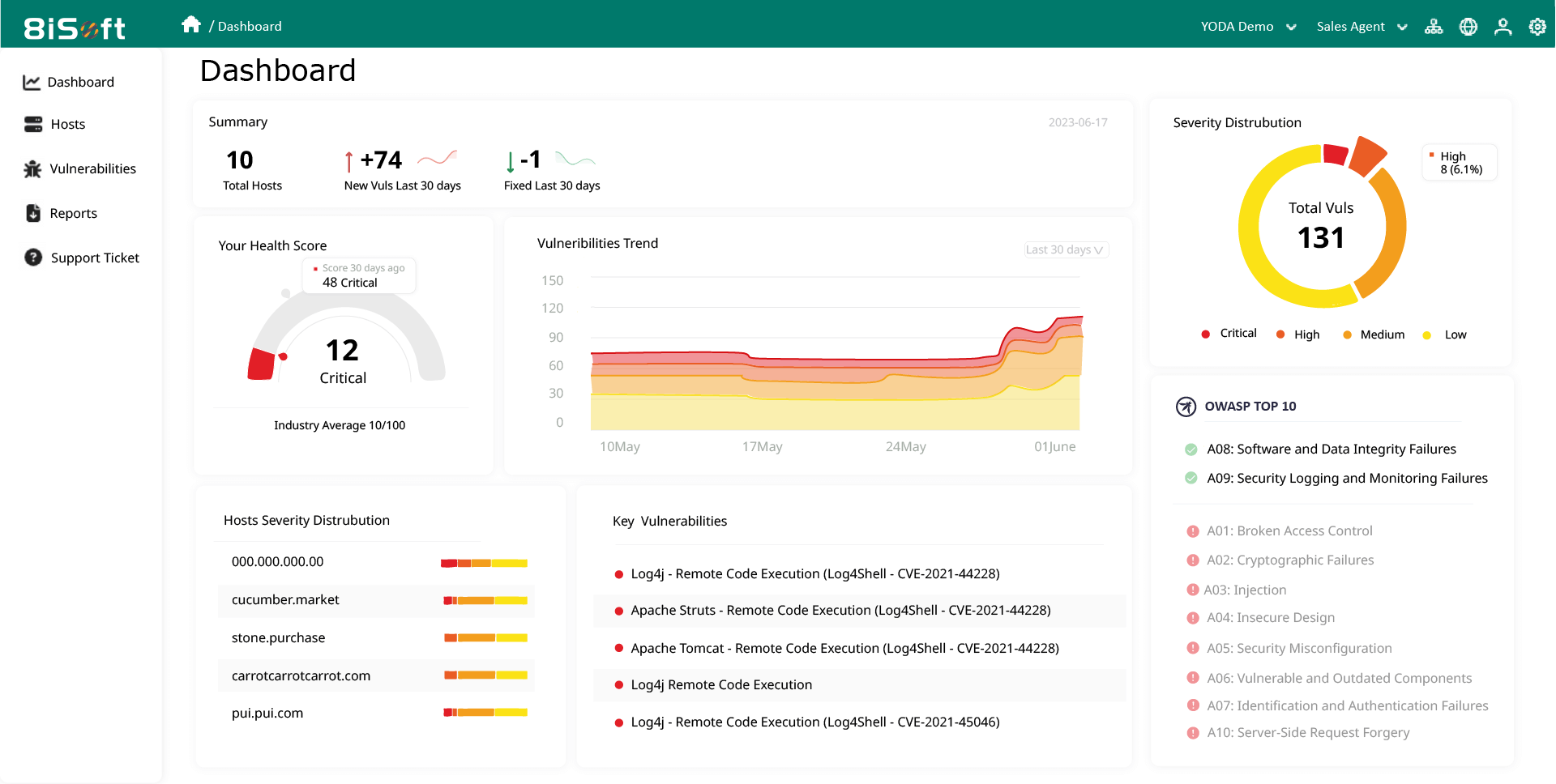

In the rapidly evolving landscape of web technologies, maintaining cybersecurity can be challenging. With our Discovery, Remediation, and Improvement (DRI) framework, 8iSoft YODA efficiently detects and manages vulnerabilities within network infrastructure. It offers customizable ISO 27001 vulnerability compliance scans, covering both internal and external assets. 8iSoft Yoda, 100% ISO 27001 compliant, assists in creating and maintaining ISO 27001 best practices.
Audit-Ready Compliance Reports and SME-Validated AI-Based Solution Steps
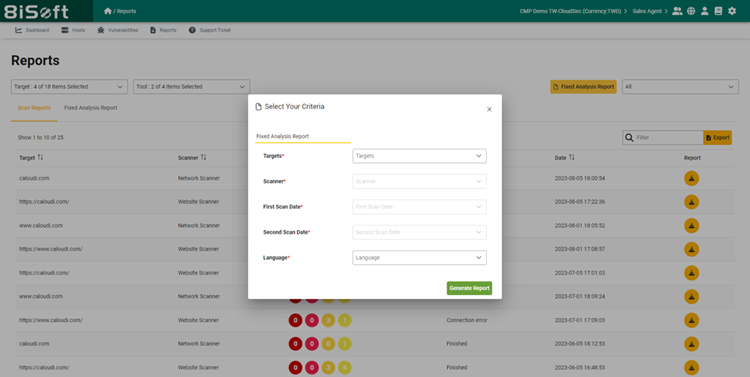
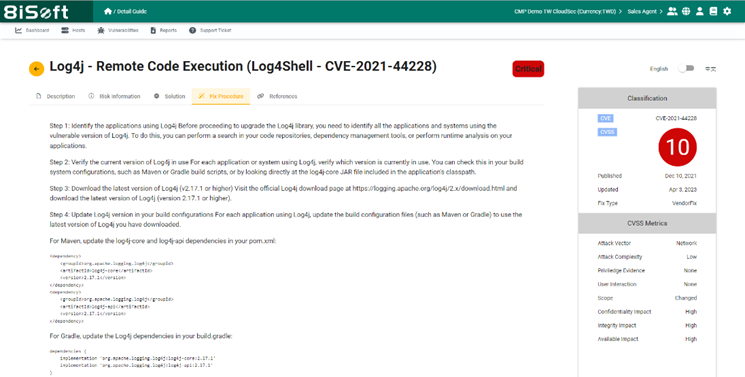
Generate comprehensive reports with 8iSoft Yoda to identify and prioritize security weaknesses. These reports offer step-by-step instructions for each risk, multiple remediation plans, and priority rankings, aligning with ISO 27001’s risk-based approach. Maintain records of actions and remediation efforts, ensuring ISO 27001 compliance.


ISO 27001 and Its 8th Domain: Operations Security
ISO 27001, an information security standard, encompasses 14 domains, each detailing guidelines for optimal security. The 8th domain, “Operations Security,” focuses on the secure operation and management of information processing facilities. Employees are urged to audit personal and work devices, upholding ISO 27001 values for information asset confidentiality and integrity.

Standard Templates from ISO
Contrary to common belief, ISO does not provide ready-made templates for compliance. ISO standards outline requirements, allowing companies to tailor processes. For ISO 27001 compliance, ensure each person’s computer is ISO compliant. 8iSoft provides a checklist, aiding in routine audits of personal devices.
Free Download!
Free ISO 27001 Personal Device Checklist Template
Access our free checklist to secure your journey to ISO 27001 certification. Protect against vulnerabilities with this accessible template. Fill out the form for immediate access.


