Top 10 Vulnerability Management Tools for Cybersecurity
Categories of Cybersecurity Tools
Cybersecurity tools are pivotal in safeguarding digital assets against a myriad of threats. These tools are diverse, spanning various functions:
- Firewalls: Monitor and control incoming/outgoing network traffic, enforcing security policies.
- Antivirus/Antimalware: Detect and remove malicious software.
- Intrusion Detection/Prevention Systems (IDS/IPS): Monitor network traffic for suspicious activity.
- SIEM (Security Information and Event Management): Collect, analyze, and detect security threats.
- Vulnerability Management Tools: Identify, assess, and manage system weaknesses.
- Endpoint Security: Protect individual devices from cyber threats.
- Identity and Access Management (IAM): Manage user access rights.
- Data Loss Prevention (DLP): Monitor and control sensitive data.
- Encryption Tools: Secure data through encryption and decryption.
- Penetration Testing Tools: Simulate cyber attacks to identify vulnerabilities.
- Security Awareness Training Platforms: Educate employees on cybersecurity best practices.
Relationship Between SIEM and Vulnerability Management Tools
Many have heard of SIEM tools but might not discern their differences from Vulnerability Management Tools. While SIEM focuses on real-time monitoring and threat detection, Vulnerability Management Tools concentrate on identifying system weaknesses proactively. SIEM collects and analyzes security data from various sources, providing an overview of potential threats, while Vulnerability Management Tools assess vulnerabilities and guide prioritization for remediation.
What Are Vulnerability Management Tools and How They Work
Vulnerability Management Tools, also known as Vulnerability Scanners, play a critical role in maintaining an organization’s security. These tools:
- Perform Vulnerability Scanning: Identify known vulnerabilities in systems, networks, and applications.
- Assess Vulnerability Severity: Evaluate the impact and risk level of identified vulnerabilities.
- Generate Comprehensive Reports: Provide detailed reports on vulnerabilities, aiding prioritization.
- Track Remediation Progress: Monitor and manage efforts to fix identified vulnerabilities.
- Offer Integration and Automation: Collaborate with other security solutions for streamlined processes.
- Provide Continuous Monitoring: Regularly scan for new vulnerabilities or security changes.
Top 10 Vulnerability Management Tools and Companies
1. 8iSoft-YODA
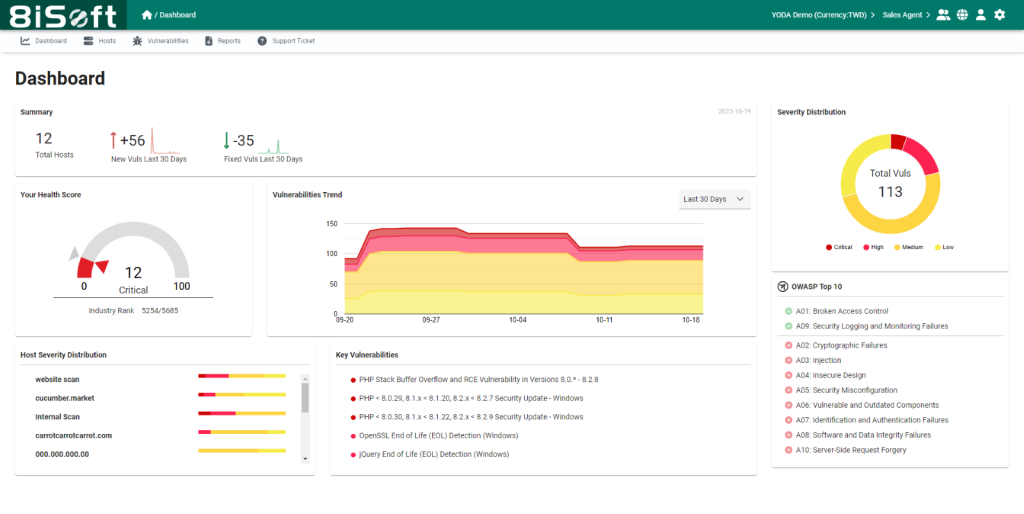

Automated website and network scanning, providing detailed plans to address vulnerabilities step by step. Tailored for SMBs, it’s scalable from 5 assets onwards. It’s designed for SMBs lacking extensive cybersecurity expertise, allowing them to monitor and remediate crucial assets efficiently.
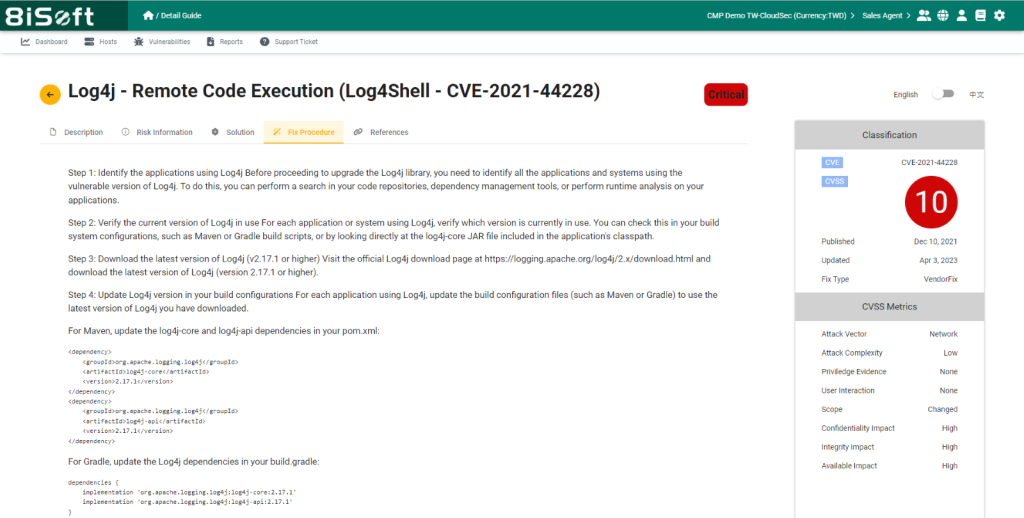

“Learn more about 8iSoft YODA and its features in our in-depth review.“
2. Rapid7 – InsightVM:
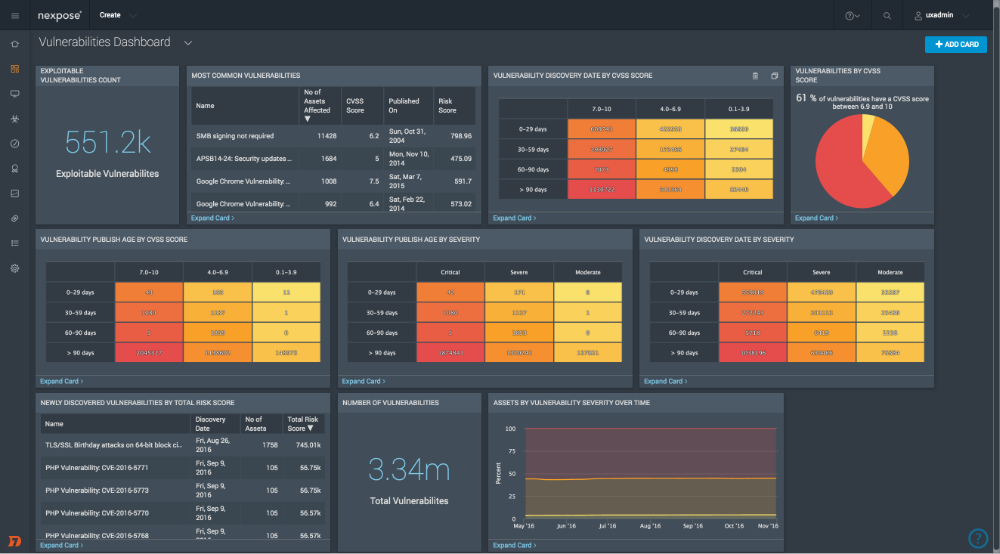

Thorough network scans to uncover vulnerabilities across endpoints and infrastructure, providing real-time risk visibility and progress tracking, fostering collaboration among teams for efficient remediation and improved security clarity.
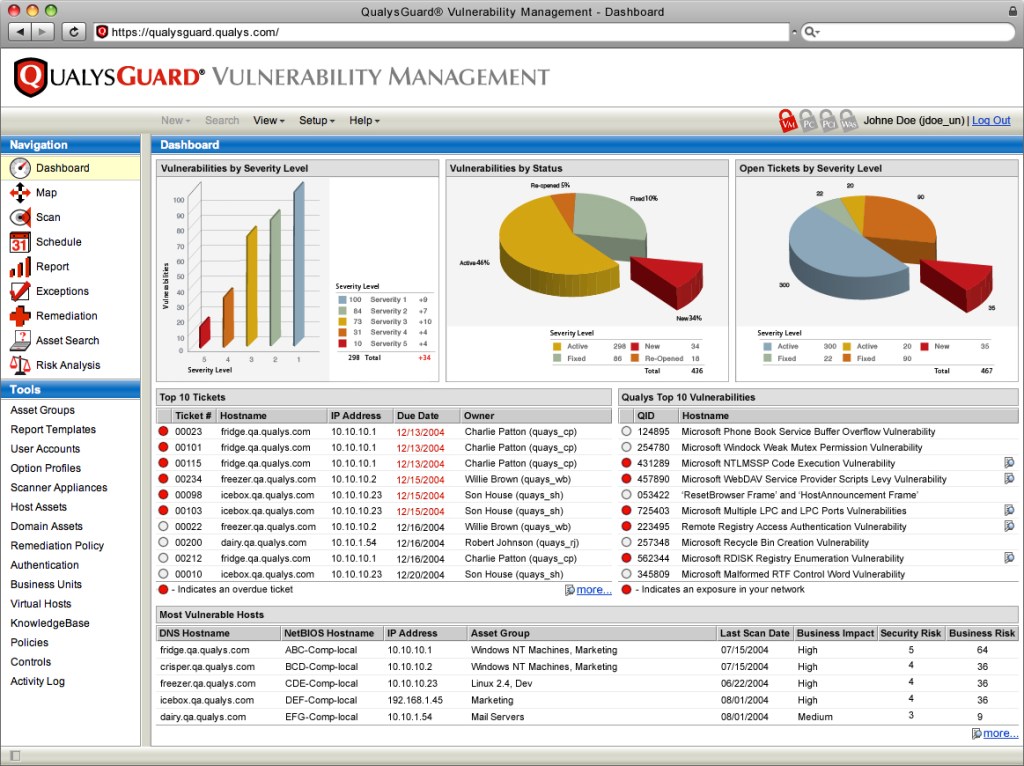
3. Qualys:
Cloud-based solutions with remote user options and real-time alerts.

4. Tenable – Nessus
Highly accessible vulnerability scanning for diverse network infrastructure.

5. Intruder
User-friendly interface and urgency-based vulnerability ranking.

6. Acunetix
Web vulnerability management scanning with over 3000 checks.

7. Burp Suite
Standard for web security professionals, offering automated testing.

8. Tripwire
Provides vulnerability assessments and customizable scanning.

9. IBM Security QRadar
Offers threat detection and compliance checks.

10. Wiz
A cloud-native platform focused on cloud service security.

Each of these tools contributes uniquely to vulnerability management, helping organizations mitigate risks and maintain a secure IT infrastructure. Explore how 8iSoft YODA and other leading tools contribute uniquely to vulnerability management, helping organizations mitigate risks and maintain a secure IT infrastructure.
